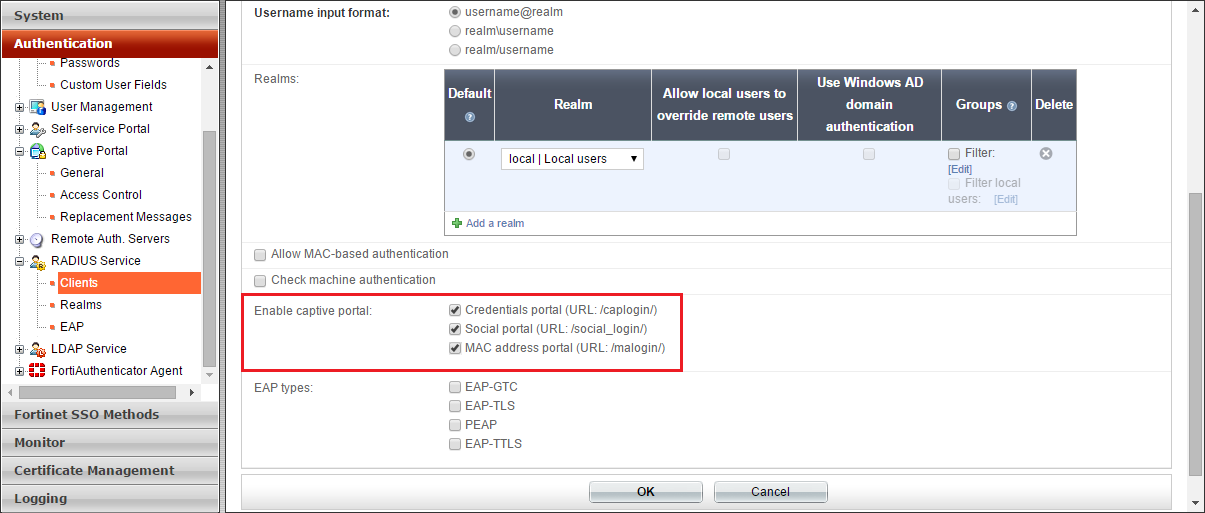
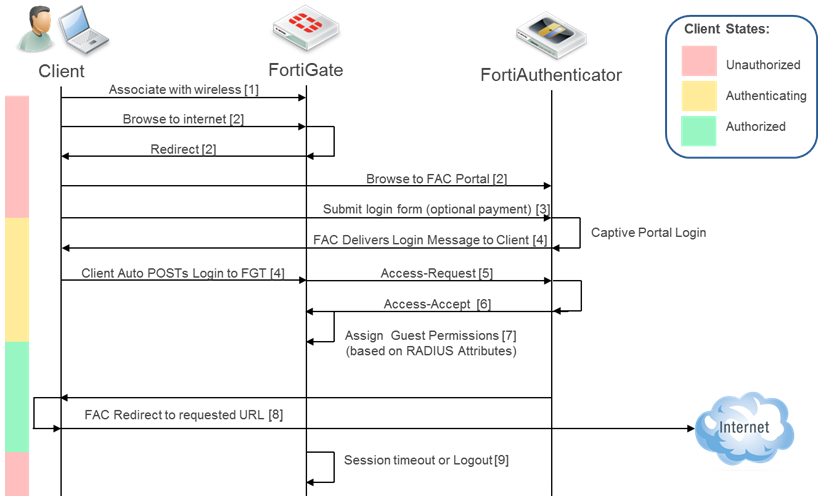
11 Describe the Use of Captive Portals
This topic discusses the following best practices for using captive portals. Captive portals are typically used by airports hotels coffee shops and other venues that offer free Wi-Fi.

Hotspot Using Captive Portal Zeroshell Linux Router
The following sections describe how use the WebUI and CLI to configure the captive portal with a proxy server.
. Public Wi-Fi hotspots with captive portals those websites where you have to accept terms and conditions or log in. Portals Raise Brand Awareness. What to do after the captive portal check.
Study of the captive portal page. You have certainly entered a mall for example and had to go through a basic registration when trying to use Wi-Fi. When you first log on to a network with a captive portal there is a web page that requires certain actions before you can access the Internet.
Android 11 will make public Wi-Fi logins easier with a new captive portal API. Android 11 Beta 2 was the first operating system to use this new captive portal API back in the summer. Packages that need to be Installed.
But captive portals work by doing exactly that. This is one of the important steps and has to be carried out keenly. They intercept and alter the connection between the user and the site they are trying to visit.
If the page was left open by Firefox you may simply close it. Captive portals are commonly used to present a landing or log-in page which may require authentication payment acceptance of an end-user license agreement acceptable use policy. End users living in MDUs where numerous guests simultaneously use the WIFI network for extended periods of time will especially appreciate this captive portal capability.
Apple has now also confirmed that iOS14 and macOS Big Sur will adopt this standard and although not generally available the API ratification signals the start of adoption across all the major operating systems. On average each captive portal uses 59 attributes max. Captive portals are to blame for a number of security issues especially when it comes to HTTPS websites.
A simple captive portal forces you to at least look at a use policy page. As for routers such as Cisco Juniper OpenWRT but. Windows provides mechanisms that can let users bypass captive portals on subsequent connection attempts.
Fortunately I had brought my Mac laptop with me on vacation and I could use it to spoof or mimic the MAC address of my Apple TV for the purposes of authenticating to the portal. End users living in MDUs where numerous guests simultaneously use the WIFI network for extended periods of time will especially appreciate this captive portal capability. The stages of this method of McCabe can be seen in table 1.
When HTTPS traffic is redirected from a proxy server to the controller the users browser will display a warning that the subject name on the certificate does not match the hostname to which the user is connecting. 47 attributes including 35 Navigator 6 Screen 3 Canvas and 3 Battery Status. A captive portal is a web page that is displayed to newly connected users of a WiFi network.
The tool that allows this is precisely the Captive Portal which controls permissions in a public or private. If this happens frequently please file a Networking bug and describe what happened requires creating a Bugzilla account. It requires some sort of interaction before granting access to network resources.
How captive portals work. Portals Raise Brand Awareness. Choose two One use for a captive portal is to allow a user to agree to specific terms and conditions in order to access network resources.
Portal Captive is a tool that controls in an automated way the entrance of visitors in a public or private network. Here are the steps which I performed on a 2020 16 MacBook Pro running macOS Big Sur 1123 which was the latest macOS as I write this. Though not its most apparent benefit the captive portal can be used as an effective marketing tool in a variety of ways.
However the captive portal is always the experience that is encountered by a first-time user. We also found 10 round10100671 hotspots fingerprint user devicebrowser before explicit consent. Which of the following describe the two main parts of a computer network security policy.
In the case of this study first the user requirement is a captive portal network with redundancy connections and a network system that can fulfill captive portal services is a MikroTik router which includes captive portal services. Because it is USB-powered I plug it into a USB battery pack when I want to be mobile eg walking around an airport. HTTPS is meant to prevent traffic interception alteration and impersonation by a third party.
When a user is presented a captive portal the user cannot establish a connection with any party to check the obtained public key as no internet is available. Captive portal prompts are displayed when you are able to manipulate this first HTTP message to return a HTTP status code of 302 redirect to the captive portal of your choice. Can be installed using apt-get Step 1.
To set up a captive portal on a Raspberry Pi you will need a wired network I will refer to this as WAN or uplink and a wireless network such as the Ralink RT5372 or. The use of captive portal is very common in public places for example airports or hotels. Though not its most apparent benefit the captive portal can be used as an effective marketing tool in a variety of ways.
This is a lot easier than hacking the MAC address each time. A captive portal is a web page accessed with a web browser that is displayed to newly connected users of a Wi-Fi or wired network before they are granted broader access to network resources. 24 round24100671 hotspots perform some form of fingerprinting.
I get on the captive portal with one device through the router and all my other devices which already know the SSID of my router are immediately on the air. Right-Click on the text area provided and select inspect Considering the browser being used is ChromeFirefox. In other words if you want to connect to a network that runs.

Captive Portal An Overview Sciencedirect Topics

Hotspot Using Captive Portal Zeroshell Linux Router

Captive Portal An Overview Sciencedirect Topics

Captive Portal An Overview Sciencedirect Topics
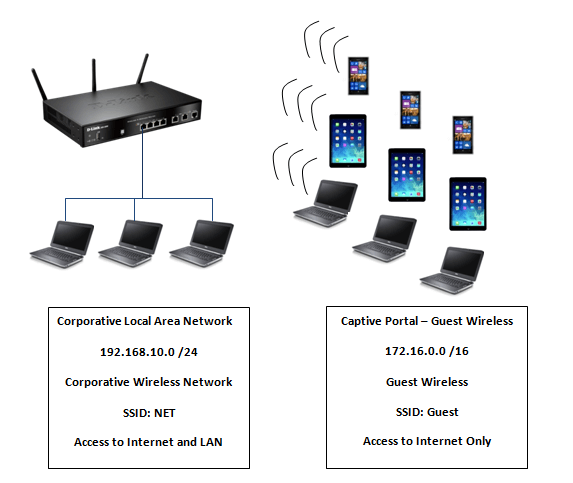
How To Setup Captive Portal Dsr Series Fw 2 X D Link Uk

Octopus Wifi Captive Portal And Wi Fi Cloud Integration Guide
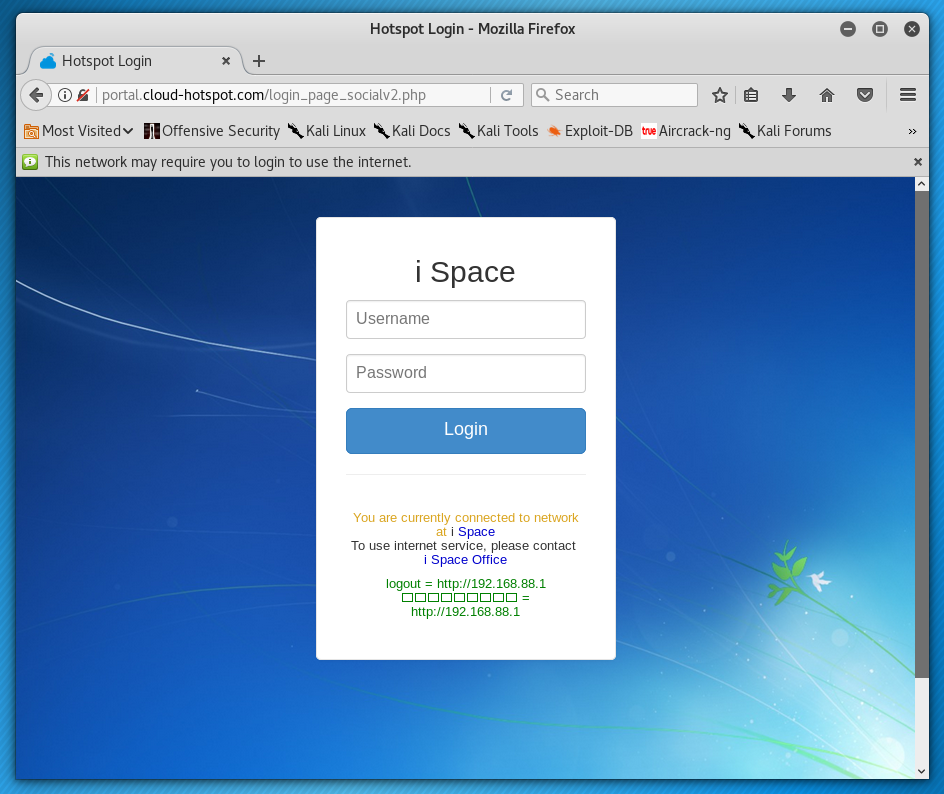
Fast And Simple Method To Bypass Captive Portal Hotspot With Authorization On The Web Interface Ethical Hacking And Penetration Testing

What Is Captive Portal What Does Captive Portal Mean Captive Portal Meaning Explanation Youtube
Linksys Official Support Configuring Captive Portal On The Linksys Lapac1750pro Ac1750 Pro Dual Band Access Point

Pfsense Captive Portal Youtube

Hotspot Using Captive Portal Zeroshell Linux Router
Linksys Official Support Configuring Captive Portal On The Linksys Lapac1750pro Ac1750 Pro Dual Band Access Point
Linksys Official Support Configuring Captive Portal On The Linksys Lapac1750pro Ac1750 Pro Dual Band Access Point

Captive Portal An Overview Sciencedirect Topics